When is the best time to catch security issues with your application? Before you’ve built it of course!
If you’re responsible for an application from a technical design perspective, the last thing you want to have happen is get all the way into the security testing process and find out that there is a major issue with your application and now the whole thing has to be redesigned!
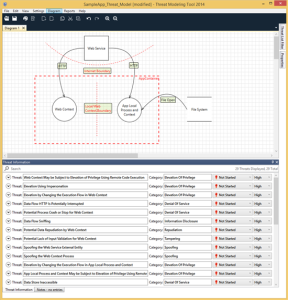
Well, now your job is even easier, thanks to the Microsoft Threat Modeling tool, and the new 2014 version that has just been released recently.
This tool lets you map out your application flows and then it will automatically analyze it for security issues.
To be frank, I’m not a massive fan of the UI appearance, but I am certainly willing to put up with it because it definitely does a quality job.
Now, whilst I would like this to be a set and forget type of deal… i.e. just put the design in, make sure it says there are no issues and then give it the greenlight, in this interesting world we live in, the bad guys are always evolving… so I’ll still continue to manually review designs and use the tool as an initial quick up front check.